TL;DR: Navigate to Settings > General > About > Certificate Trust Settings and turn the switch on for your custom certificate.
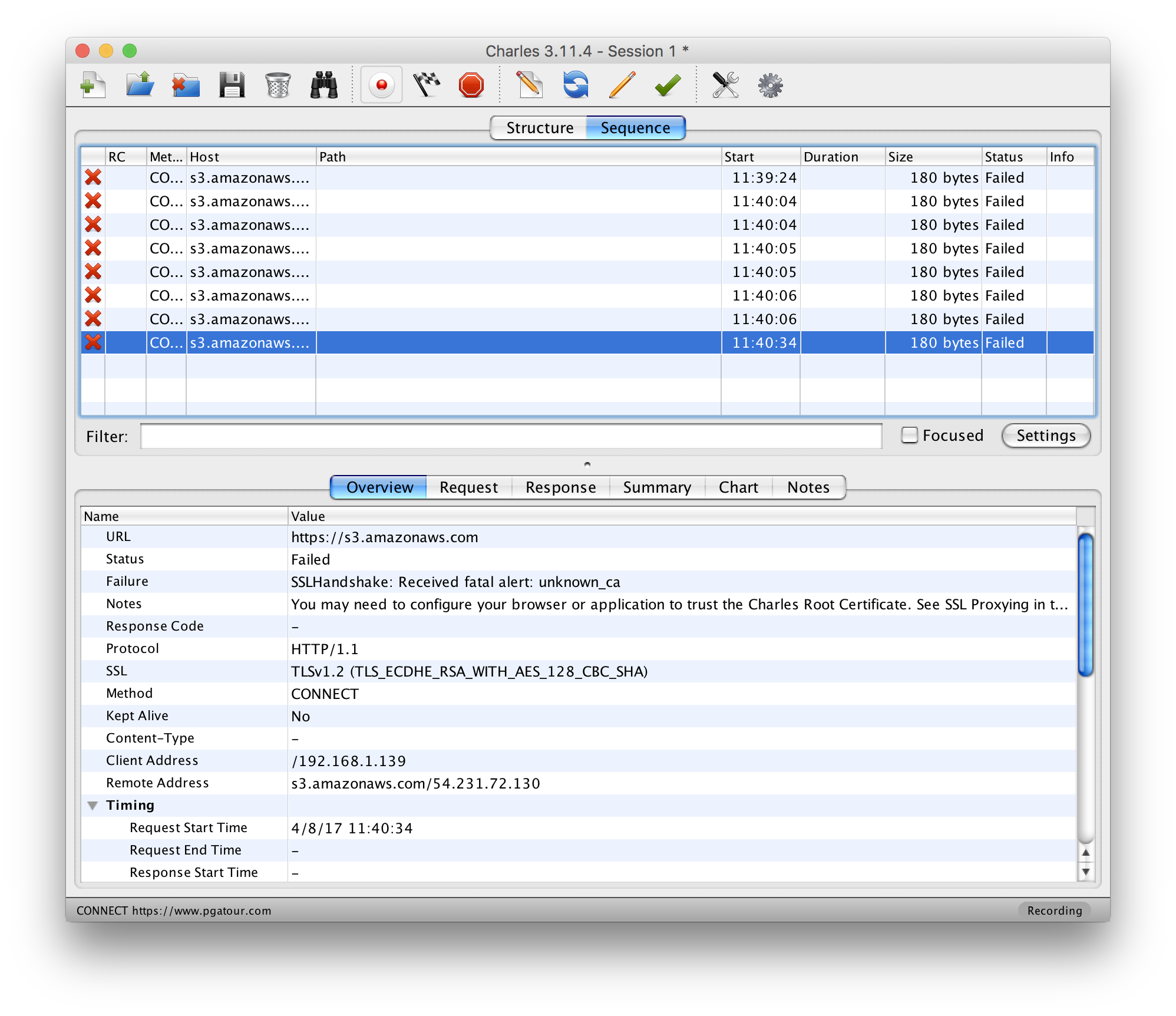
Like many, Charles Proxy has become an indispensable part of my daily toolkit. Every person on my QA team uses it daily for their projects. Recently while testing on iOS 10.3, one of my team members couldn’t get his SSL traffic to proxy. Usually when somebody runs into this, it’s because the person hasn’t installed the Charles Proxy root certificate on the device they’re trying to proxy. Then why you try to proxy SSL traffic in Charles you’ll the following error: SSLHandshake: Received fatal alert: unknown_ca
Charles Proxy will even offer a helpful suggestion:
You may need to configure your browser or application to trust the Charles Root Certificate. See SSL Proxying in the Help menu.
iOS is refusing the SSL handshake because the certificate authority that has issued the SSL certificate being used is not in its Trust Store. Previously to resolve this, we would just need to go to http://ssl.charles in Safari on the device, and we could then install the root CA from Charles and tell the device we want to trust it. In this case, the QA person had already taken these steps. After some digging around, he found the problem.
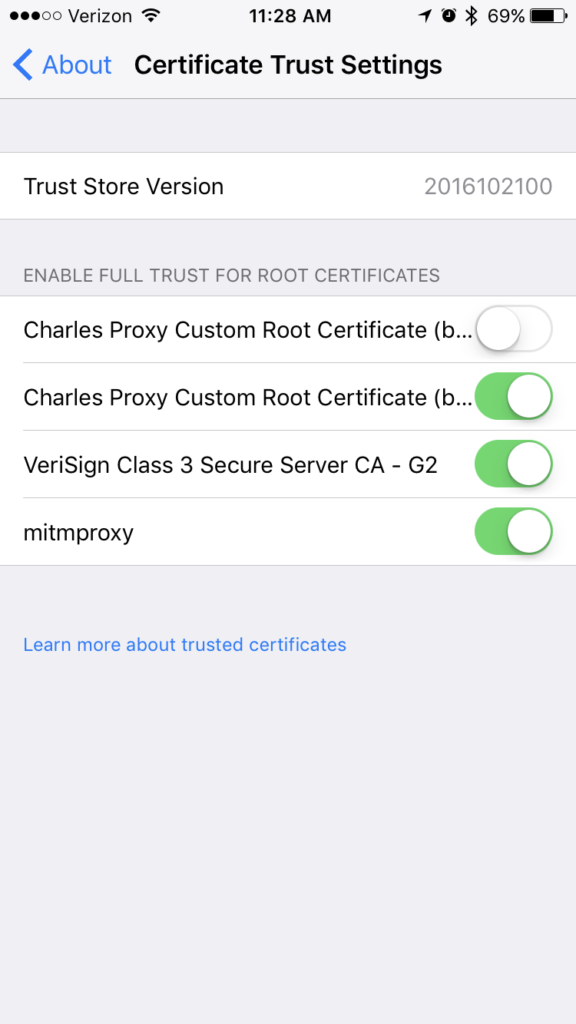
Settings > General > About > Certificate Trust Testings
The Charles Proxy Custom Root Certificate that he had installed showed up in the list, but its toggle was turned off. While this section existed prior to iOS 10.3, by default when you would install a custom certificate, iOS would implicitly trust it. No further action required. As of iOS 10.3, the default for new custom certificates is to not trust them. If you want to trust the custom certificate you’ve installed (why else would you have installed it?), you’ll need to navigate to the section mentioned above and manually turn the switch on to trust the certificate. Any certificates installed and trusted prior to iOS 10.3 seem to be grandfathered in, so you won’t run into this until you’re trying to use a new root certificate.